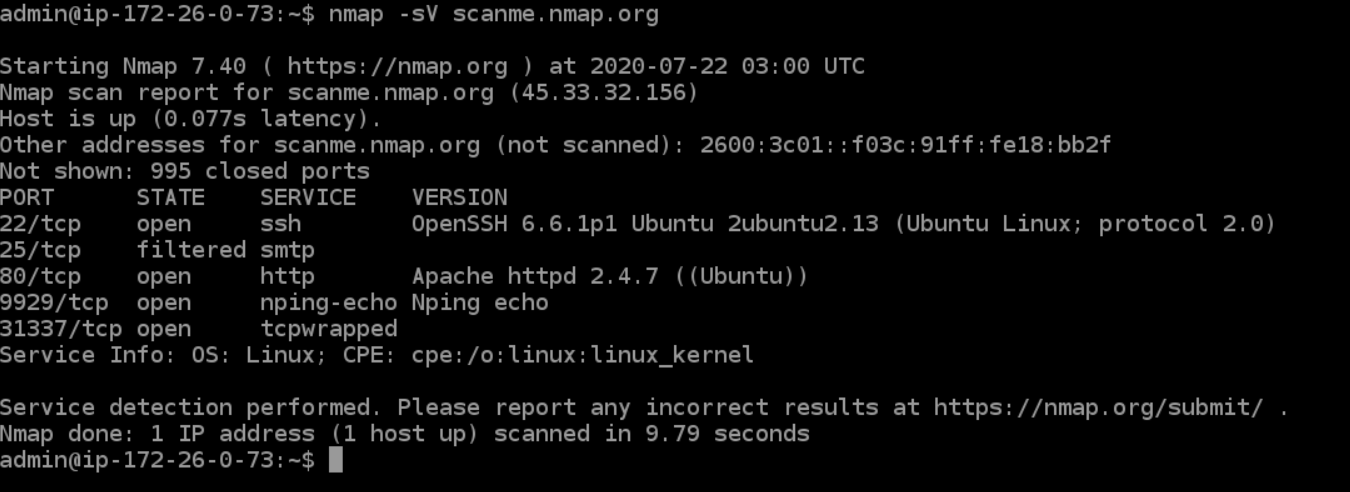
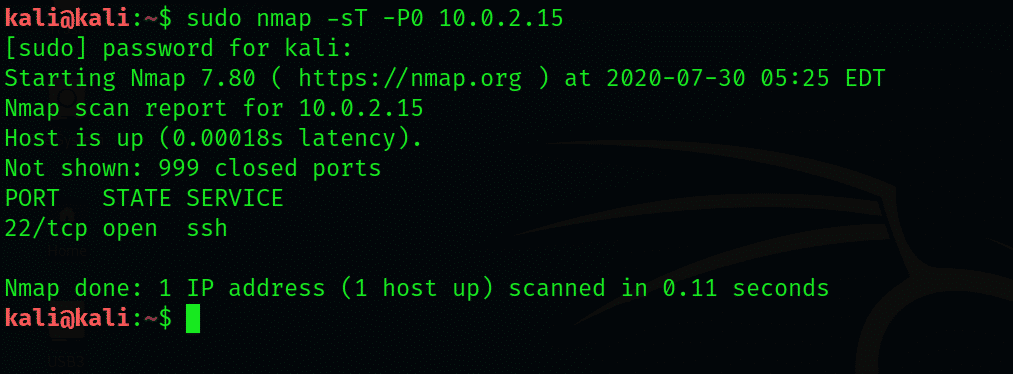
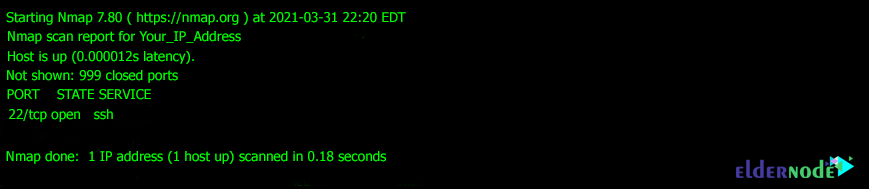
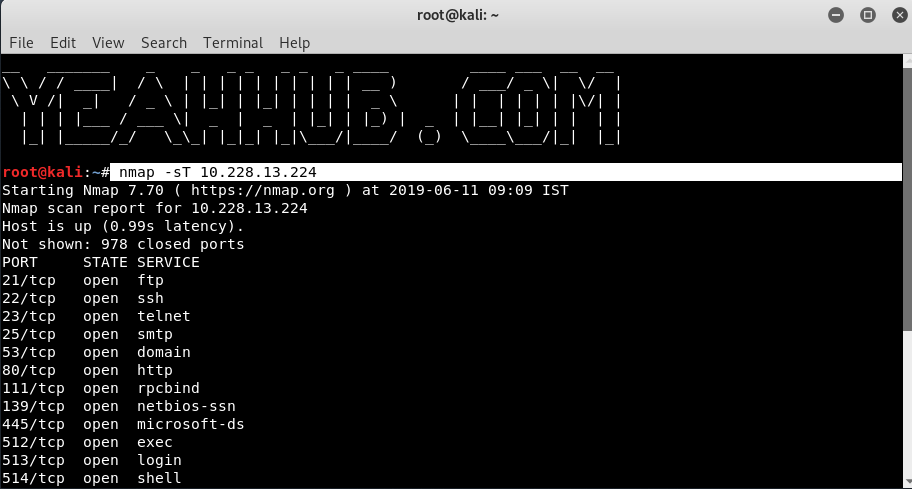
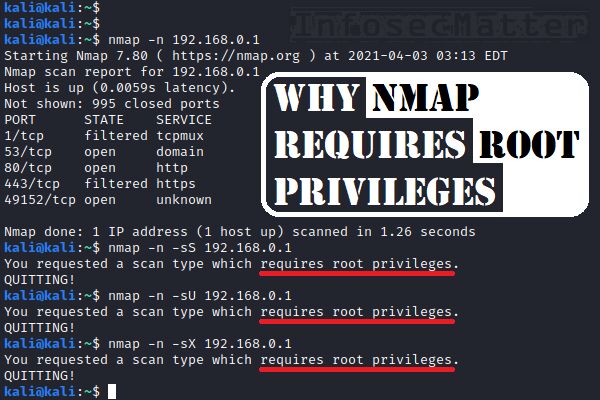
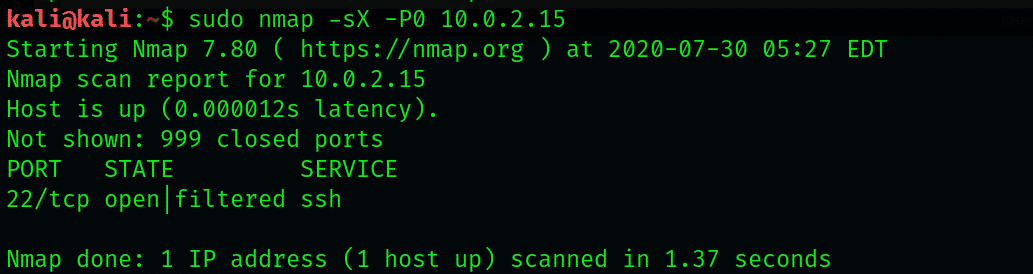
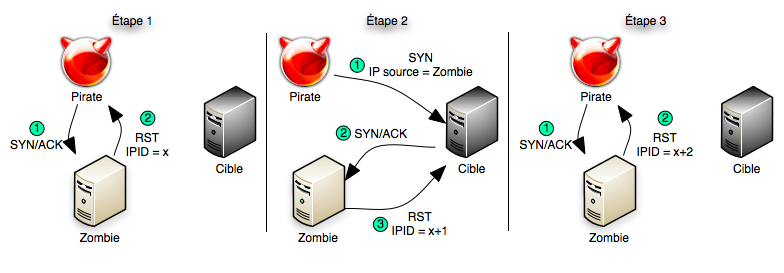
Scan networks using Nmap |Nmap detailed Tutorial|bypass firewall using Nmap |stealth scan | by freaky DODO | The Startup | Medium

David Bombal on Twitter: "Your First Nmap Scan #nmap #network #scanner #tool #portscanner #hacking #hacker #hackingtools #cybersecurity #scanning # scan #port #portscanning #gathering #cyber #security https://t.co/IRDK5u8AML" / Twitter

How to use NMAP – which is the “right” NMAP scan to use? | University of South Wales: Cyber University of the year: Three years running: 2019, 2020, 2021
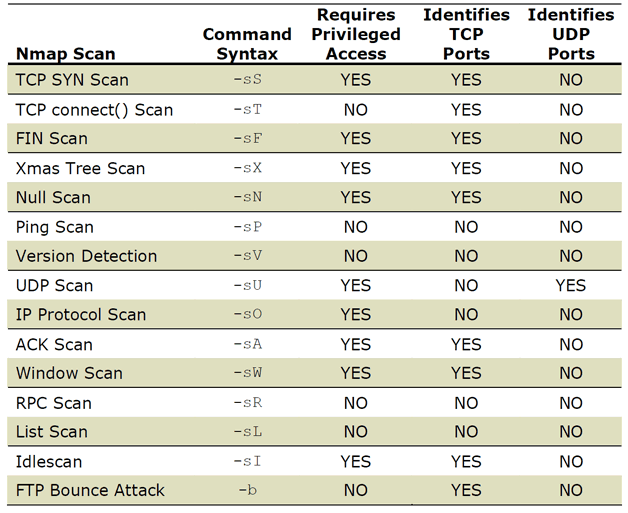
Optimizing Your Nmap Scan: Nmap Scanning Methods - Professor Messer IT Certification Training Courses