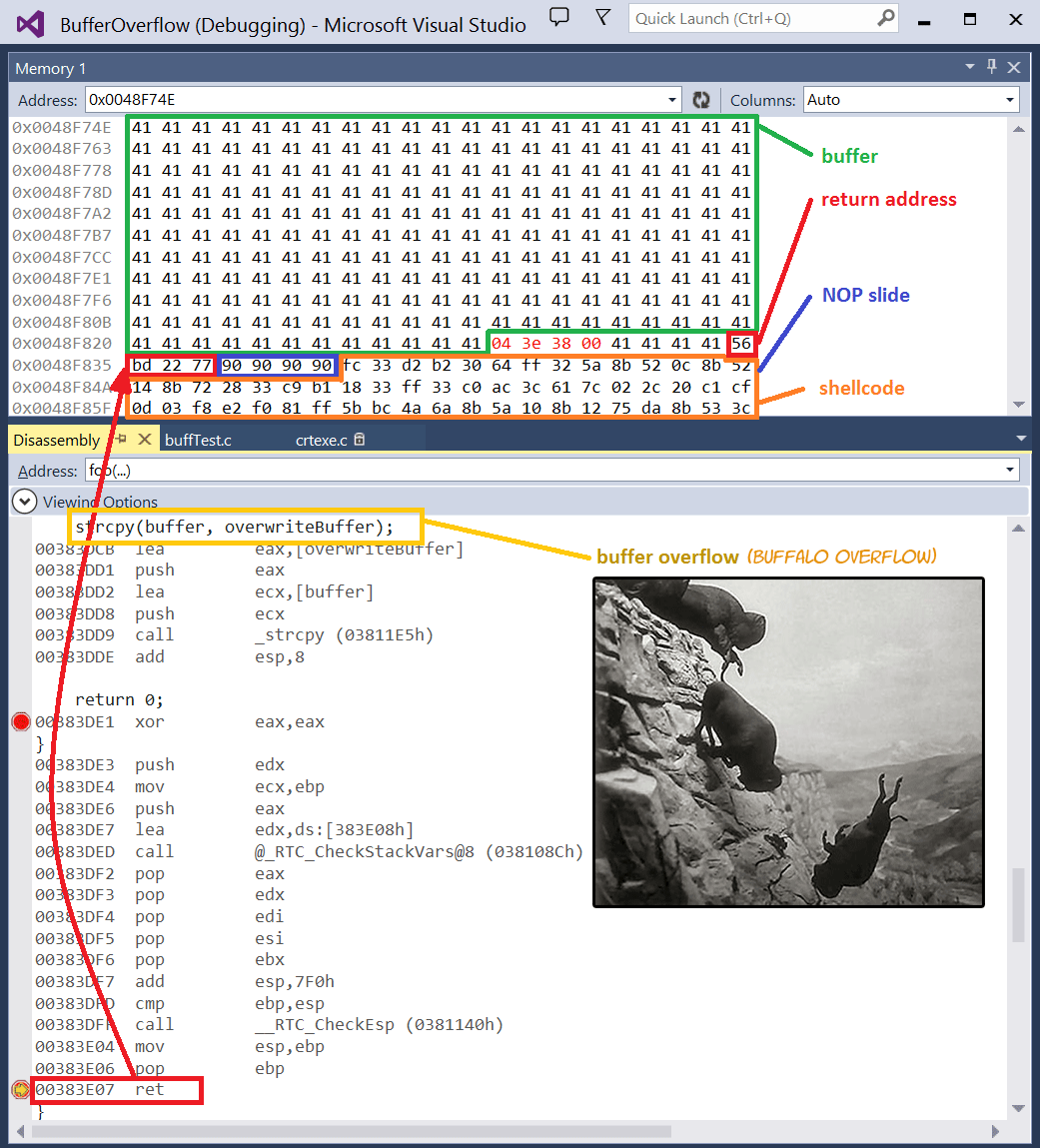
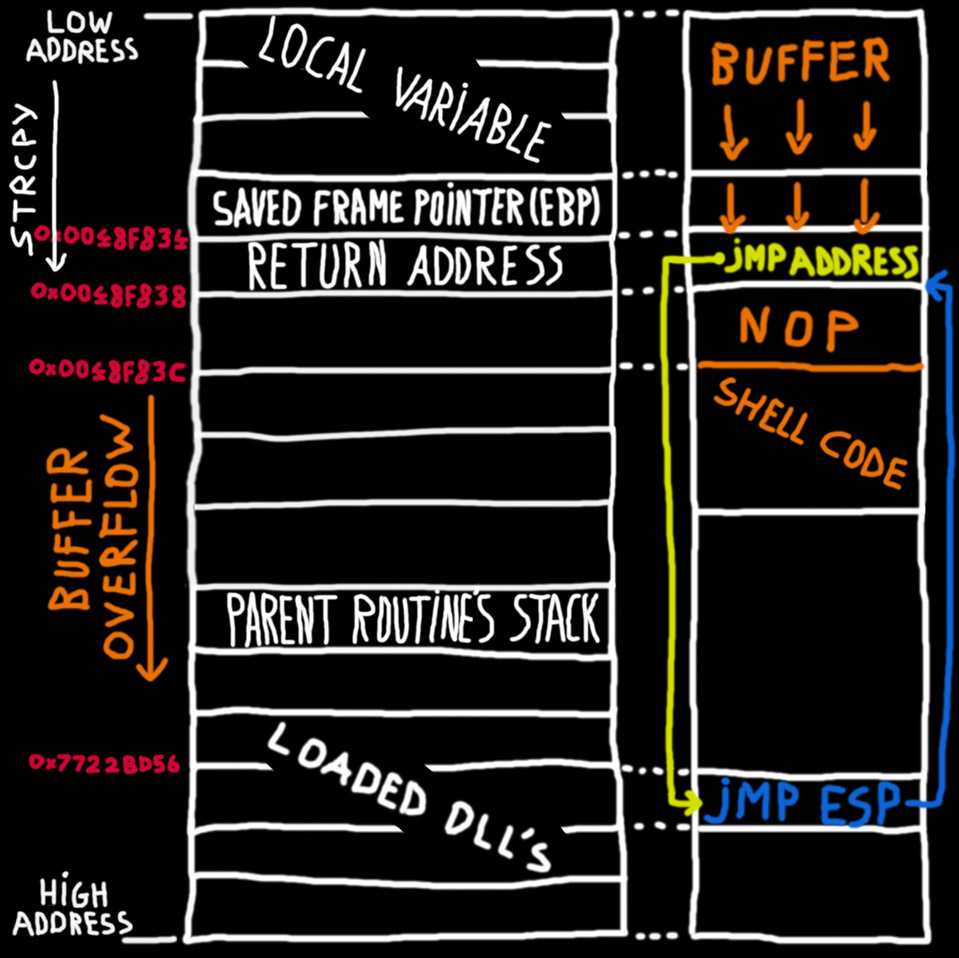
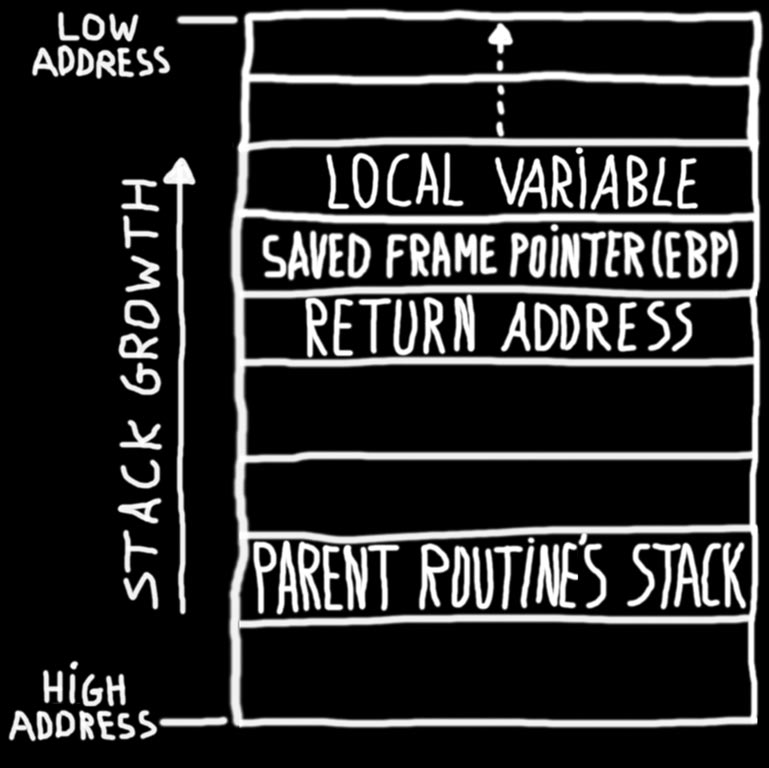
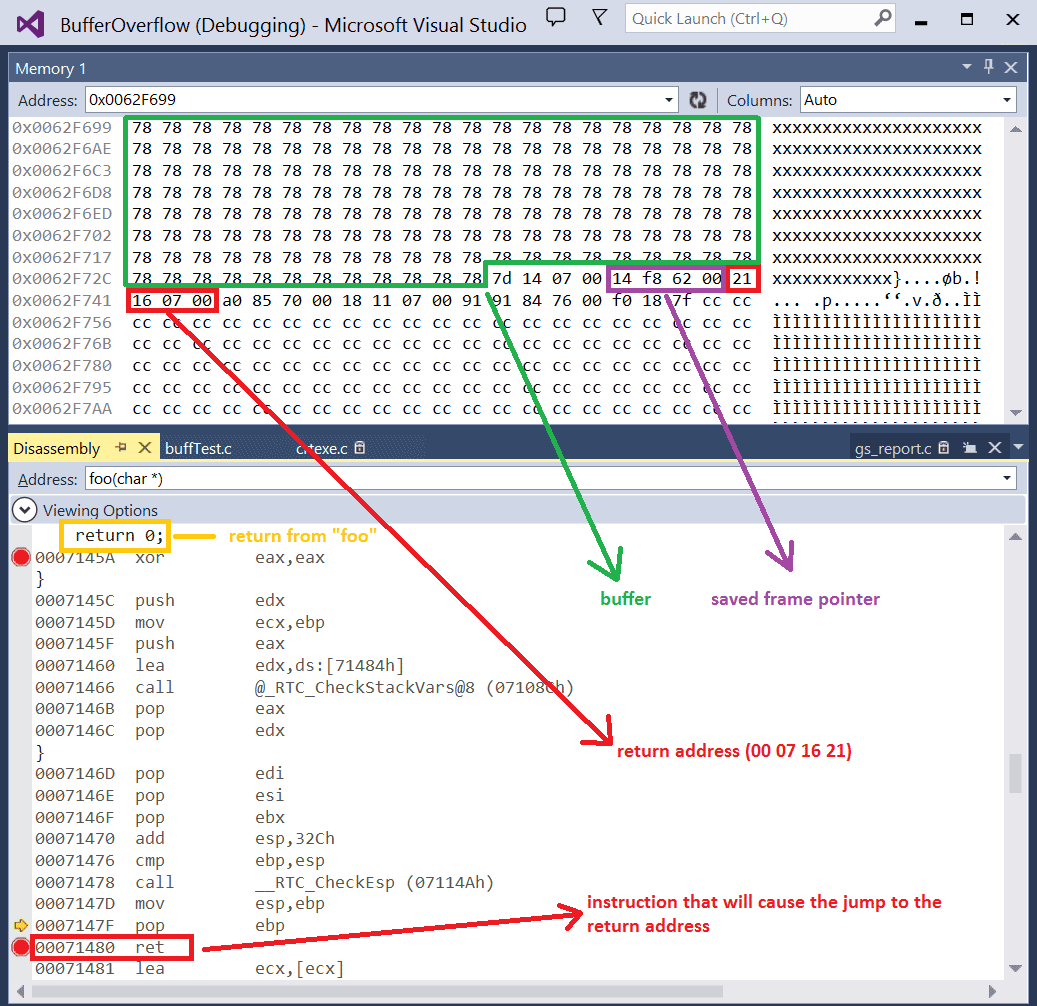
Lab 3 report - Ankit Kumar 773312668 Buffer Overflow Vulnerability Lab Report Task 1 Non-root stack program Debug stack Figure 1.1 Return address = | Course Hero

An introduction to computer buffer overflow problem on using unsecured C or C++ standard functions in C programs

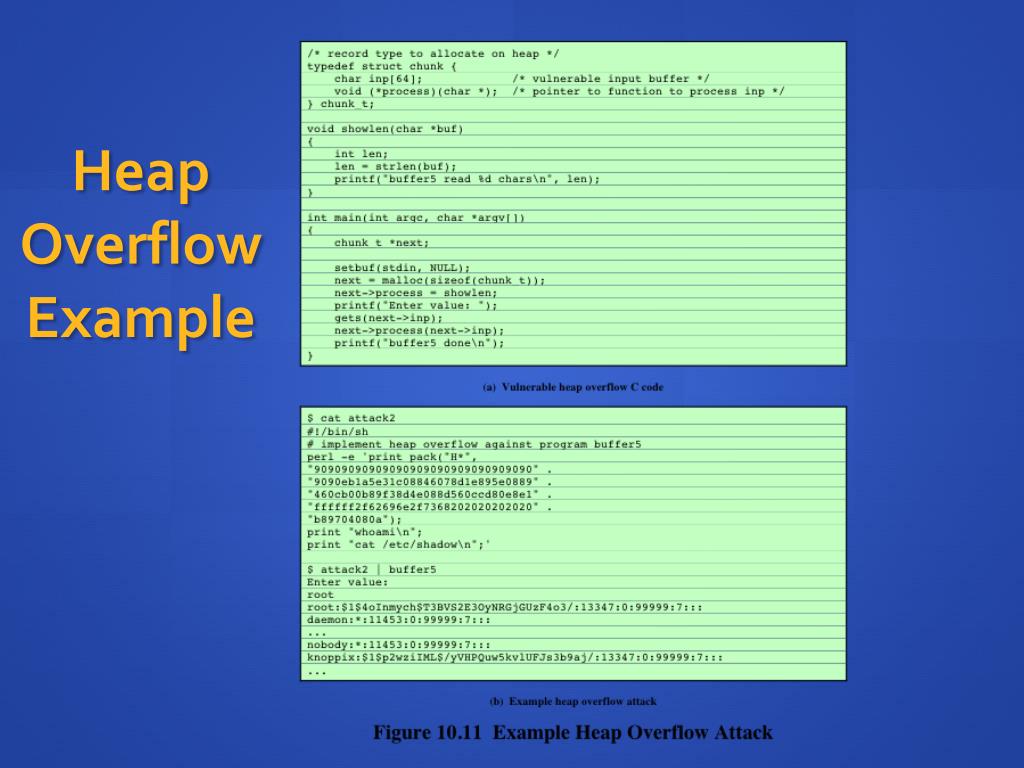
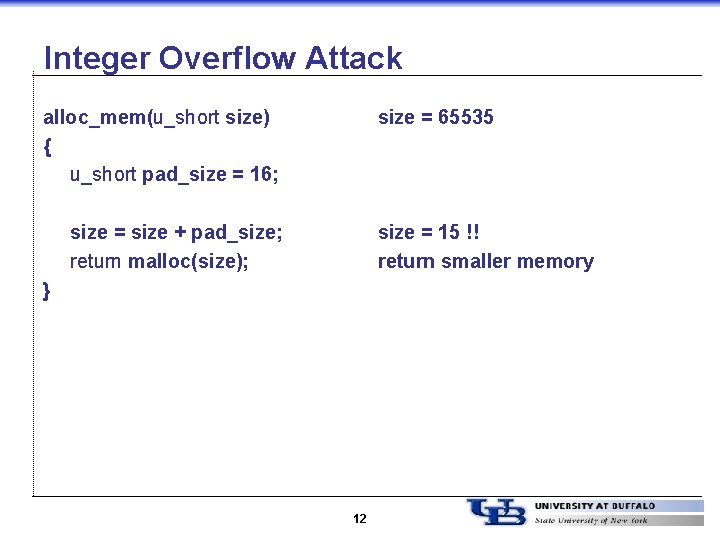
Buffer Overflows: Attacks and Defenses for the Vulnerability of the Decade Crispin Cowan SANS ppt download
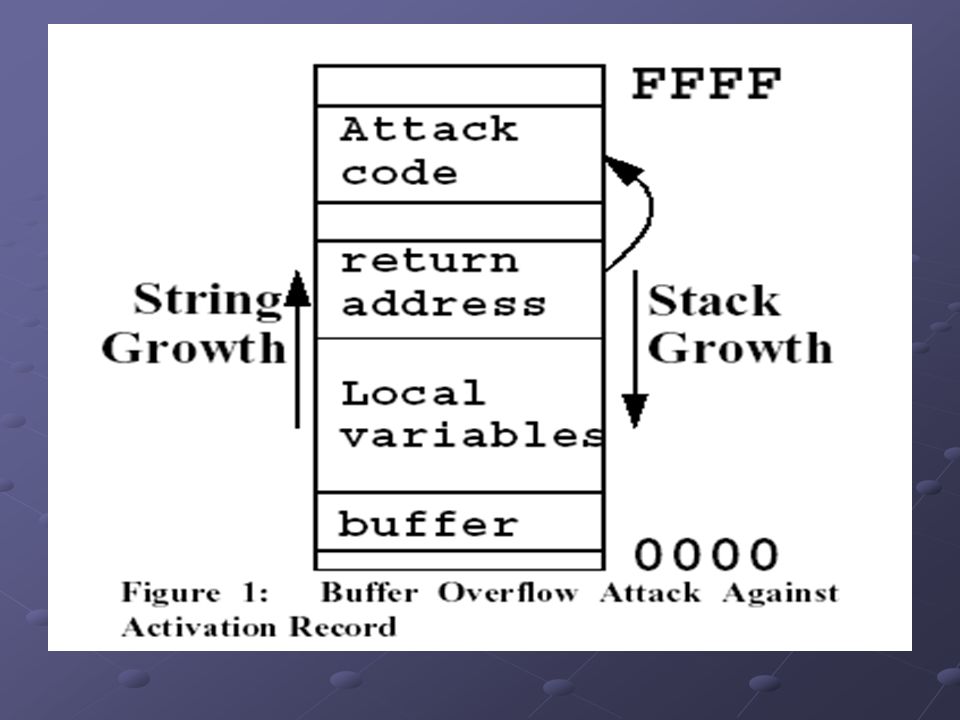
Buffer Overflows: Attacks and Defenses for the Vulnerability of the Decade Crispin Cowan SANS ppt download